which of the following are breach prevention best practices jko
Create Strong Policies Strong Passwords. 30 Best Practices for Preventing a Data Breach.
The employees play an essential responsibility in keeping their.

. Invest in the Right. Which of the following are breach prevention best practices. A breach as defined by the DoD is broader than a HIPAA breach.
Data encryption solutions to render data inaccessible and unusable in. Which of the following are breach prevention best practices. Developing the IRP will help the IT staff of the company to control the data breach incidents.
Identify areas that store transmit collect or process. Data loss protection DLP to detect and prevent data breaches by blocking the extraction of sensitive information. D All Of The Above.
In the age of digital data keeping information safe is more important than ever. Identity sensitive data collected stored transmitted or processes. Making weak passwords can be a reason for Data.
Best Practices for Preventing a Data BreachTrain Employees on Security Awareness. Employees have an important role in keeping their organizations secure. Select the best answer.
Which of the following are. Which of the following are breach prevention best practices. Train Employees on Security Awareness.
At all levels should implement. Which of the following are breach prevention best practices. Which of the following are breach prevention best practices.
All of the above.

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero

Answered Hipaa And Privacy Act Training Challenge Exam Dha Us001 Exams Nursing Docsity

Which Of The Following Are Breach Prevention Best Practices Public Health

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero
Hipaa And Privacy Act Training 1 5 Hrs Jko Flashcards Quizlet
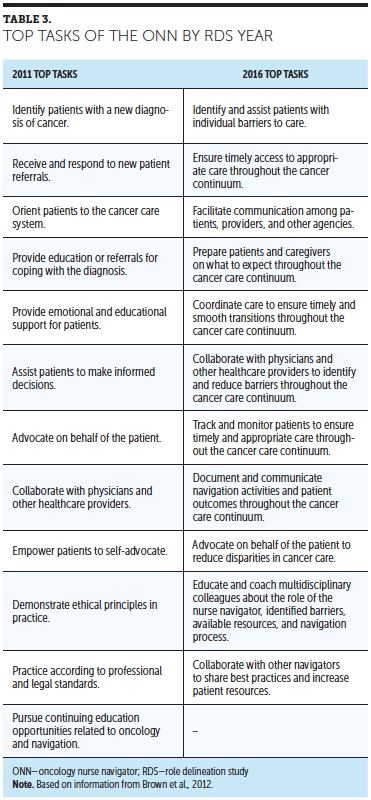
Oncology Nurse Navigation Results Of The 2016 Role Delineation Study Ons
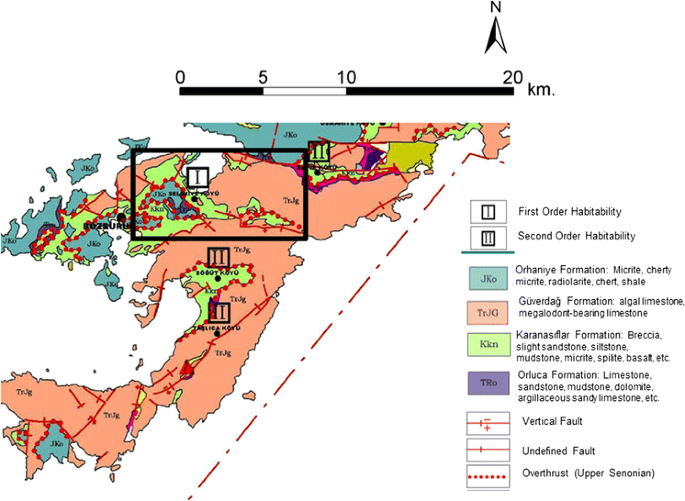
Searching Ancient Territorium Of Hygassos In Anatolia Settlement Patterns And Spatio Temporal Investigations Through Aerial And Gis Applications Springerlink

Dod Cyber Awareness Challenge 2020 Your Ultimate Guide Infosec Insights

Biorestorative Therapies Inc Ipo Investment Prospectus S 1

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

Hipaa M5 Docx Select The Best Answer Which Of The Following Are Common Causes Of Breaches All Of The Above When Must A Breach Be Reported To The Course Hero

6 Which Of The Following Statements About The Privacy Act Are True All Of The Course Hero

Scientific Program Of 34th World Congress Of Endourology Swl Program Book And Abstracts Journal Of Endourology

Near Field Communication Nfc Technology Vulnerabilities And Principal Attack Schema Infosec Resources

Which Of The Following Are Breach Prevention Best Practices Public Health
Equal Opportunity Policy Basic Training Jko Flashcards Quizlet